Using AWS CloudFormation and AWS Cloud Development Kit to provision multicloud resources
September 9, 2023Customers often need to architect solutions to support components across multiple cloud service providers, a need which may arise if they have acquired a company running on another cloud, or for functional purposes where specific services provide a differentiated capability. In this post, we will show you how to use the AWS Cloud Development Kit (AWS CDK) to create a single pane of glass for managing your multicloud resources.
AWS CDK is an open source framework that builds on the underlying functionality provided by AWS CloudFormation. It allows developers to define cloud resources using common programming languages and an abstraction model based on reusable components called constructs. There is a misconception that CloudFormation and CDK can only be used to provision resources on AWS, but this is not the case. The CloudFormation registry, with support for third party resource types, along with custom resource providers, allow for any resource that can be configured via an API to be created and managed, regardless of where it is located.
Multicloud solution design paradigm
Multicloud solutions are often designed with services grouped and separated by cloud, creating a segregation of resource and functions within the design. This approach leads to a duplication of layers of the solution, most commonly a duplication of resources and the deployment processes for each environment. This duplication increases cost, and leads to a complexity of management increasing the potential break points within the solution or practice.
Along with simplifying resource deployments, and the ever-increasing complexity of customer needs, so too has the need increased for the capability of IaC solutions to deploy resources across hybrid or multicloud environments. Through meeting this need, a proliferation of supported tools, frameworks, languages, and practices has created “choice overload”. At worst, this scares the non-cloud-savvy away from adopting an IaC solution benefiting their cloud journey, and at best confuses the very reason for adopting an IaC practice.
A single pane of glass
Systems Thinking is a holistic approach that focuses on the way a system’s constituent parts interrelate and how systems work as a whole especially over time and within the context of larger systems. Systems thinking is commonly accepted as the backbone of a successful systems engineering approach. Designing solutions taking a full systems view, based on the component’s function and interrelation within the system across environments, more closely aligns with the ability to handle the deployment of each cloud-specific resource, from a single control plane.
While AWS provides a list of services that can be used to help design, manage and operate hybrid and multicloud solutions, with AWS as the primary cloud you can go beyond just using services to support multicloud. CloudFormation registry resource types model and provision resources using custom logic, as a component of stacks in CloudFormation. Public extensions are not only provided by AWS, but third-party extensions are made available for general use by publishers other than AWS, meaning customers can create their own extensions and publish them for anyone to use.
The AWS CDK, which has a 1:1 mapping of all AWS CloudFormation resources, as well as a library of abstracted constructs, supports the ability to import custom AWS CloudFormation extensions, enabling customers and partners to create custom AWS CDK constructs for their extensions. The chosen programming language can be used to inherit and abstract the custom resource into reusable AWS CDK constructs, allowing developers to create solutions that contain native AWS extensions along with secondary hybrid or alternate cloud resources.
Providing the ability to integrate mixed resources in the same stack more closely aligns with the functional design and often diagrammatic depiction of the solution. In essence, we are creating a single IaC pane of glass over the entire solution, deployed through a single control plane. This lowers the complexity and the cost of maintaining separate modules and deployment pipelines across multiple cloud providers.
A common use case for a multicloud: disaster recovery
One of the most common use cases of the requirement for using components across different cloud providers is the need to maintain data sovereignty while designing disaster recovery (DR) into a solution.
Data sovereignty is the idea that data is subject to the laws of where it is physically located, and in some countries extends to regulations that if data is collected from citizens of a geographical area, then the data must reside in servers located in jurisdictions of that geographical area or in countries with a similar scope and rigor in their protection laws.
This requires organizations to remain in compliance with their host country, and in cases such as state government agencies, a stricter scope of within state boundaries, data sovereignty regulations. Unfortunately, not all countries, and especially not all states, have multiple AWS regions to select from when designing where their primary and recovery data backups will reside. Therefore, the DR solution needs to take advantage of multiple cloud providers in the same geography, and as such a solution must be designed to backup or replicate data across providers.
The multicloud solution
A multicloud solution to the proposed use case would be the backup of data from an AWS resource such as an Amazon S3 bucket to another cloud provider within the same geography, such as an Azure Blob Storage container, using AWS event driven behaviour to trigger the copying of data from the primary AWS resource to the secondary Azure backup resource.
Following the IaC single pane of glass approach, the Azure Blob Storage container is created as a resource type in the CloudFormation Registry, and imported into the AWS CDK to be used as a construct in the solution. However, before the extension resource type can be used effectively in the CDK as a reusable construct and added to your private library, you will first need to go through the import into CDK process for creating Constructs.
There are three different levels of constructs, beginning with low-level constructs, which are called CFN Resources (or L1, short for “layer 1”). These constructs directly represent all resources available in AWS CloudFormation. They are named CfnXyz, where Xyz is name of the resource.
Layer 1 Construct
In this example, an L1 construct named CfnAzureBlobStorage represents an Azure::BlobStorage AWS CloudFormation extension. Here you also explicitly configure the ref property, in order for higher level constructs to access the Output value which will be the Azure blob container url being provisioned.
import { CfnResource } from "aws-cdk-lib";
import { Secret, ISecret } from "aws-cdk-lib/aws-secretsmanager";
import { Construct } from "constructs"; export interface CfnAzureBlobStorageProps { subscriptionId: string; clientId: string; tenantId: string; clientSecretName: string;
} // L1 Construct
export class CfnAzureBlobStorage extends Construct { // Allows accessing the ref property public readonly ref: string; constructor(scope: Construct, id: string, props: CfnAzureBlobStorageProps) { super(scope, id); const secret = this.getSecret("AzureClientSecret", props.clientSecretName); const azureBlobStorage = new CfnResource( this, "ExtensionAzureBlobStorage", { type: "Azure::BlobStorage", properties: { AzureSubscriptionId: props.subscriptionId, AzureClientId: props.clientId, AzureTenantId: props.tenantId, AzureClientSecret: secret.secretValue.unsafeUnwrap() }, } ); this.ref = azureBlobStorage.ref; } private getSecret(id: string, secretName: string) : ISecret { return Secret.fromSecretNameV2(this, secretName.concat("Value"), secretName); }
}
As with every CDK Construct, the constructor arguments are scope, id and props. scope and id are propagated to the cdk.Construct base class. The props argument is of type CfnAzureBlobStorageProps which includes four properties all of type string. This is how the Azure credentials are propagated down from upstream constructs.
Layer 2 Construct
The next level of constructs, L2, also represent AWS resources, but with a higher-level, intent-based API. They provide similar functionality, but incorporate the defaults, boilerplate, and glue logic you’d be writing yourself with a CFN Resource construct. They also provide convenience methods that make it simpler to work with the resource.
In this example, an L2 construct is created to abstract the CfnAzureBlobStorage L1 construct and provides additional properties and methods.
import { Construct } from "constructs";
import { CfnAzureBlobStorage } from "./cfn-azure-blob-storage"; // L2 Construct
export class AzureBlobStorage extends Construct { public readonly blobContainerUrl: string; constructor( scope: Construct, id: string, subscriptionId: string, clientId: string, tenantId: string, clientSecretName: string ) { super(scope, id); const azureBlobStorage = new CfnAzureBlobStorage( this, "CfnAzureBlobStorage", { subscriptionId: subscriptionId, clientId: clientId, tenantId: tenantId, clientSecretName: clientSecretName, } ); this.blobContainerUrl = azureBlobStorage.ref; }
}
The custom L2 construct class is declared as AzureBlobStorage, this time without the Cfn prefix to represent an L2 construct. This time the constructor arguments include the Azure credentials and client secret, and the ref from the L1 construct us output to the public variable AzureBlobContainerUrl.
As an L2 construct, the AzureBlobStorage construct could be used in CDK Apps along with AWS Resource Constructs in the same Stack, to be provisioned through AWS CloudFormation creating the IaC single pane of glass for a multicloud solution.
Layer 3 Construct
The true value of the CDK construct programming model is in the ability to extend L2 constructs, which represent a single resource, into a composition of multiple constructs that provide a solution for a common task. These are Layer 3, L3, Constructs also known as patterns.
In this example, the L3 construct represents the solution architecture to backup objects uploaded to an Amazon S3 bucket into an Azure Blob Storage container in real-time, using AWS Lambda to process event notifications from Amazon S3.
import { RemovalPolicy, Duration, CfnOutput } from "aws-cdk-lib";
import { Bucket, BlockPublicAccess, EventType } from "aws-cdk-lib/aws-s3";
import { DockerImageFunction, DockerImageCode } from "aws-cdk-lib/aws-lambda";
import { PolicyStatement, Effect } from "aws-cdk-lib/aws-iam";
import { LambdaDestination } from "aws-cdk-lib/aws-s3-notifications";
import { IStringParameter, StringParameter } from "aws-cdk-lib/aws-ssm";
import { Secret, ISecret } from "aws-cdk-lib/aws-secretsmanager";
import { Construct } from "constructs";
import { AzureBlobStorage } from "./azure-blob-storage"; // L3 Construct
export class S3ToAzureBackupService extends Construct { constructor( scope: Construct, id: string, azureSubscriptionIdParamName: string, azureClientIdParamName: string, azureTenantIdParamName: string, azureClientSecretName: string ) { super(scope, id); // Retrieve existing SSM Parameters const azureSubscriptionIdParameter = this.getSSMParameter("AzureSubscriptionIdParam", azureSubscriptionIdParamName); const azureClientIdParameter = this.getSSMParameter("AzureClientIdParam", azureClientIdParamName); const azureTenantIdParameter = this.getSSMParameter("AzureTenantIdParam", azureTenantIdParamName); // Retrieve existing Azure Client Secret const azureClientSecret = this.getSecret("AzureClientSecret", azureClientSecretName); // Create an S3 bucket const sourceBucket = new Bucket(this, "SourceBucketForAzureBlob", { removalPolicy: RemovalPolicy.RETAIN, blockPublicAccess: BlockPublicAccess.BLOCK_ALL, }); // Create a corresponding Azure Blob Storage account and a Blob Container const azurebBlobStorage = new AzureBlobStorage( this, "MyCustomAzureBlobStorage", azureSubscriptionIdParameter.stringValue, azureClientIdParameter.stringValue, azureTenantIdParameter.stringValue, azureClientSecretName ); // Create a lambda function that will receive notifications from S3 bucket // and copy the new uploaded object to Azure Blob Storage const copyObjectToAzureLambda = new DockerImageFunction( this, "CopyObjectsToAzureLambda", { timeout: Duration.seconds(60), code: DockerImageCode.fromImageAsset("copy_s3_fn_code", { buildArgs: { "--platform": "linux/amd64" } }), }, ); // Add an IAM policy statement to allow the Lambda function to access the // S3 bucket sourceBucket.grantRead(copyObjectToAzureLambda); // Add an IAM policy statement to allow the Lambda function to get the contents // of an S3 object copyObjectToAzureLambda.addToRolePolicy( new PolicyStatement({ effect: Effect.ALLOW, actions: ["s3:GetObject"], resources: [`arn:aws:s3:::${sourceBucket.bucketName}/*`], }) ); // Set up an S3 bucket notification to trigger the Lambda function // when an object is uploaded sourceBucket.addEventNotification( EventType.OBJECT_CREATED, new LambdaDestination(copyObjectToAzureLambda) ); // Grant the Lambda function read access to existing SSM Parameters azureSubscriptionIdParameter.grantRead(copyObjectToAzureLambda); azureClientIdParameter.grantRead(copyObjectToAzureLambda); azureTenantIdParameter.grantRead(copyObjectToAzureLambda); // Put the Azure Blob Container Url into SSM Parameter Store this.createStringSSMParameter( "AzureBlobContainerUrl", "Azure blob container URL", "/s3toazurebackupservice/azureblobcontainerurl", azurebBlobStorage.blobContainerUrl, copyObjectToAzureLambda ); // Grant the Lambda function read access to the secret azureClientSecret.grantRead(copyObjectToAzureLambda); // Output S3 bucket arn new CfnOutput(this, "sourceBucketArn", { value: sourceBucket.bucketArn, exportName: "sourceBucketArn", }); // Output the Blob Conatiner Url new CfnOutput(this, "azureBlobContainerUrl", { value: azurebBlobStorage.blobContainerUrl, exportName: "azureBlobContainerUrl", }); } }The custom L3 construct can be used in larger IaC solutions by calling the class called S3ToAzureBackupService and providing the Azure credentials and client secret as properties to the constructor.
import * as cdk from "aws-cdk-lib";
import { Construct } from "constructs";
import { S3ToAzureBackupService } from "./s3-to-azure-backup-service"; export class MultiCloudBackupCdkStack extends cdk.Stack { constructor(scope: Construct, id: string, props?: cdk.StackProps) { super(scope, id, props); const s3ToAzureBackupService = new S3ToAzureBackupService( this, "MyMultiCloudBackupService", "/s3toazurebackupservice/azuresubscriptionid", "/s3toazurebackupservice/azureclientid", "/s3toazurebackupservice/azuretenantid", "s3toazurebackupservice/azureclientsecret" ); }
}
Solution Diagram
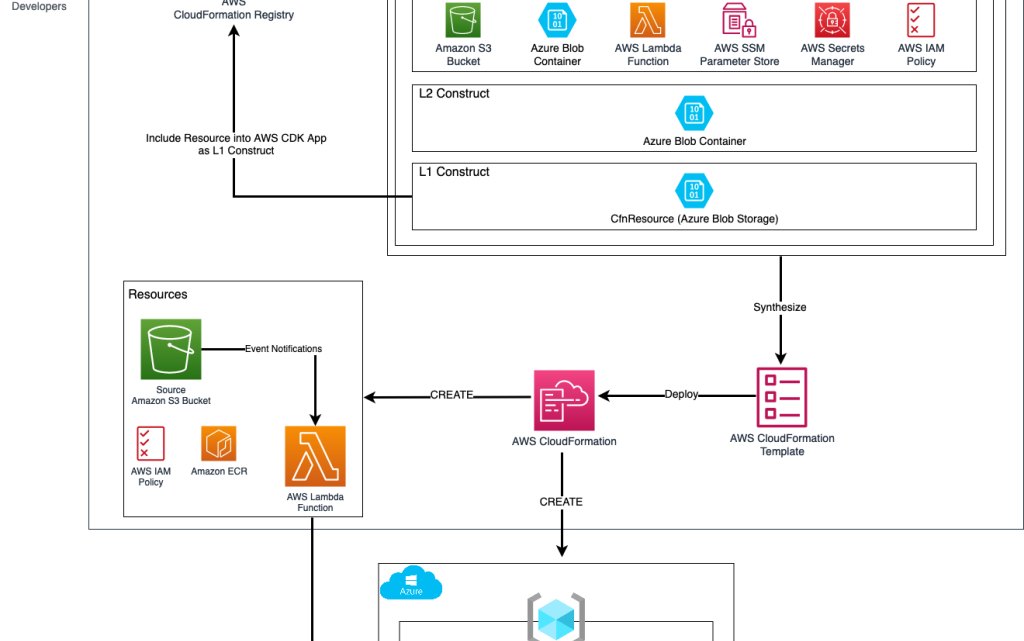
Diagram 1: IaC Single Control Plane, demonstrates the concept of the Azure Blob Storage extension being imported from the AWS CloudFormation Registry into AWS CDK as an L1 CfnResource, wrapped into an L2 Construct and used in an L3 pattern alongside AWS resources to perform the specific task of backing up from and Amazon s3 Bucket into an Azure Blob Storage Container.

Diagram 1: IaC Single Control Plan
The CDK application is then synthesized into one or more AWS CloudFormation Templates, which result in the CloudFormation service deploying AWS resource configurations to AWS and Azure resource configurations to Azure.
This solution demonstrates not only how to consolidate the management of secondary cloud resources into a unified infrastructure stack in AWS, but also the improved productivity by eliminating the complexity and cost of operating multiple deployment mechanisms into multiple public cloud environments.
The following video demonstrates an example in real-time of the end-state solution:
Next Steps
While this was just a straightforward example, with the same approach you can use your imagination to come up with even more and complex scenarios where AWS CDK can be used as a single pane of glass for IaC to manage multicloud and hybrid solutions.
To get started with the solution discussed in this post, this workshop will provide you with the instructions you need to understand the steps required to create the S3ToAzureBackupService.
Once you have learned how to create AWS CloudFormation extensions and develop them into AWS CDK Constructs, you will learn how, with just a few lines of code, you can develop reusable multicloud unified IaC solutions that deploy through a single AWS control plane.
Conclusion
By adopting AWS CloudFormation extensions and AWS CDK, deployed through a single AWS control plane, the cost and complexity of maintaining deployment pipelines across multiple cloud providers is reduced to a single holistic solution-focused pipeline. The techniques demonstrated in this post and the related workshop provide a capability to simplify the design of complex systems, improve the management of integration, and more closely align the IaC and deployment management practices with the design.
About the authors:
